DNS rewrite or DNS Doctoring has been around on the Cisco ASA’s for a while. Palo Alto firewalls received this feature in 9.0.2.
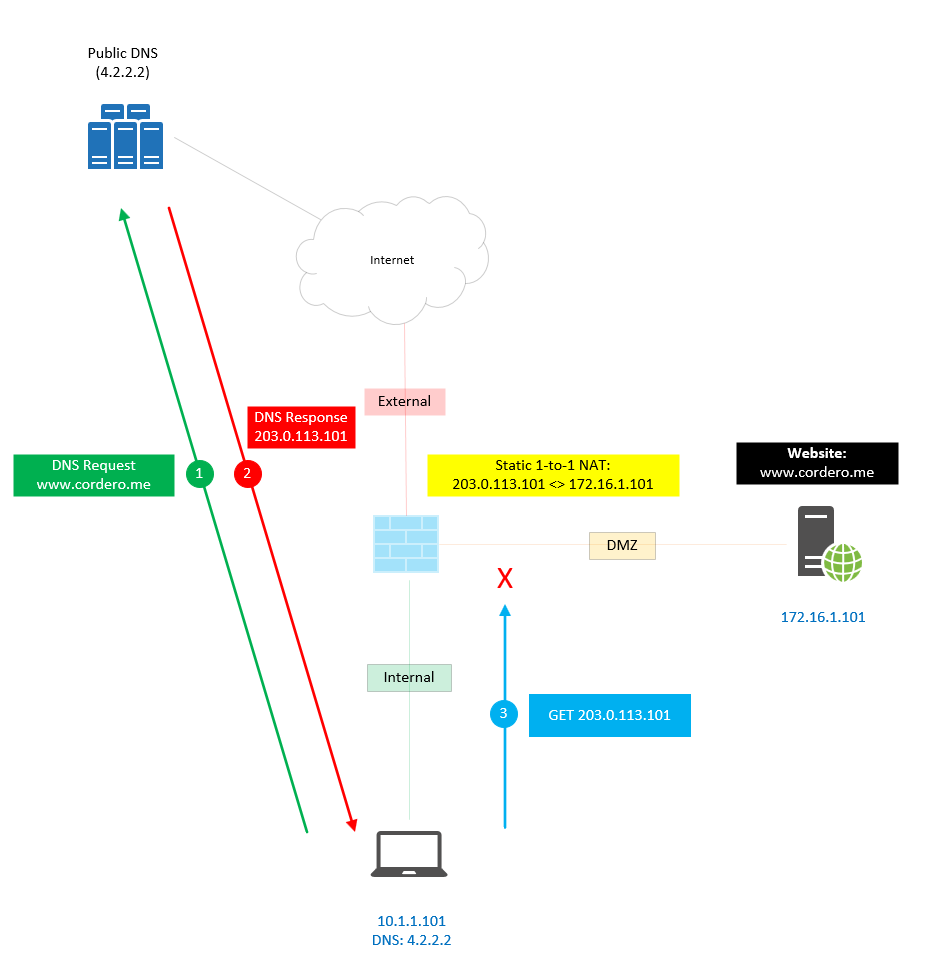
Let’s take a look at what DNS looks like without this feature. It’s straightforward—basic DNS functionality. Below we can see the DNS is resolving to a Public IP and that traffic from the Internal Network to the DMZ is not allowed on the Firewall.
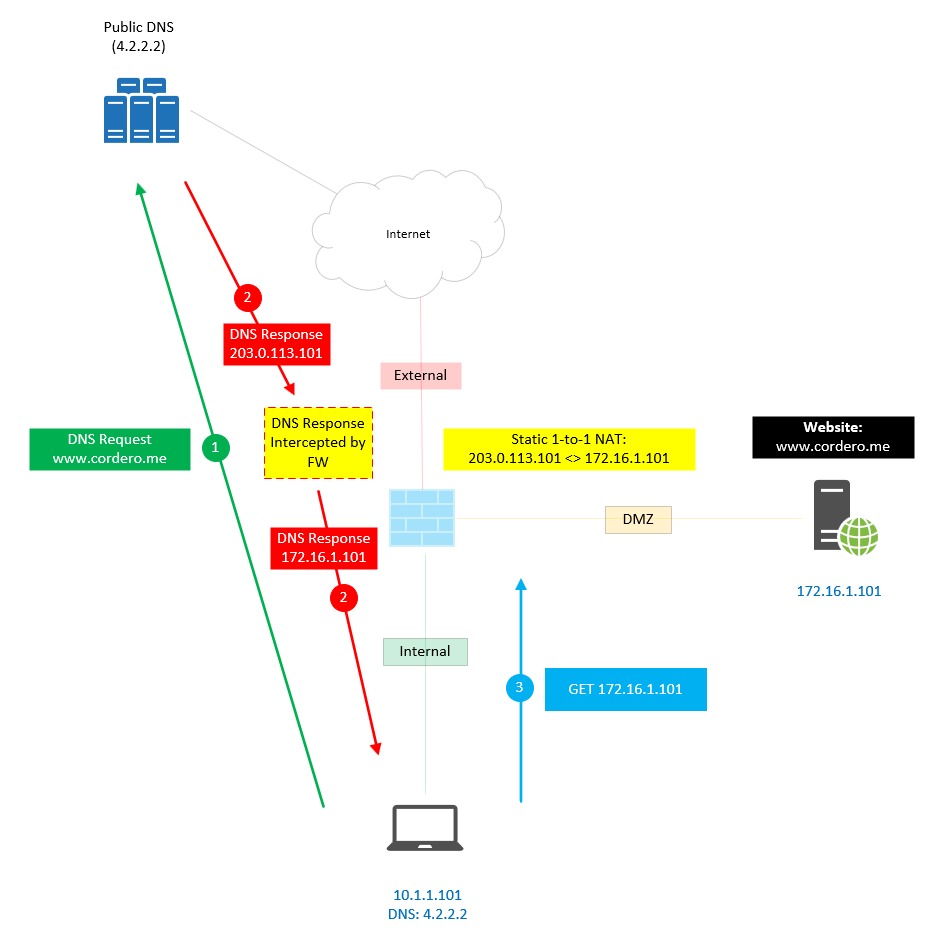
When we enable the feature, we can see that the Firewall will intercept the DNS Response and change it to the IP you want or configured. Now that the IP is a Private IP, it is allowed from the Internal Network to the DMZ.
You could create the Zone on your internal DNS, but it will be one more thing to manage since you will have to create a record on both the Public and Internal DNS servers.
Something you might want to experiment with is different ways to implement this feature. Remember, this feature is a band-aid or temporary solution that should be used when something like integrations happens where you have overlapping subnets.
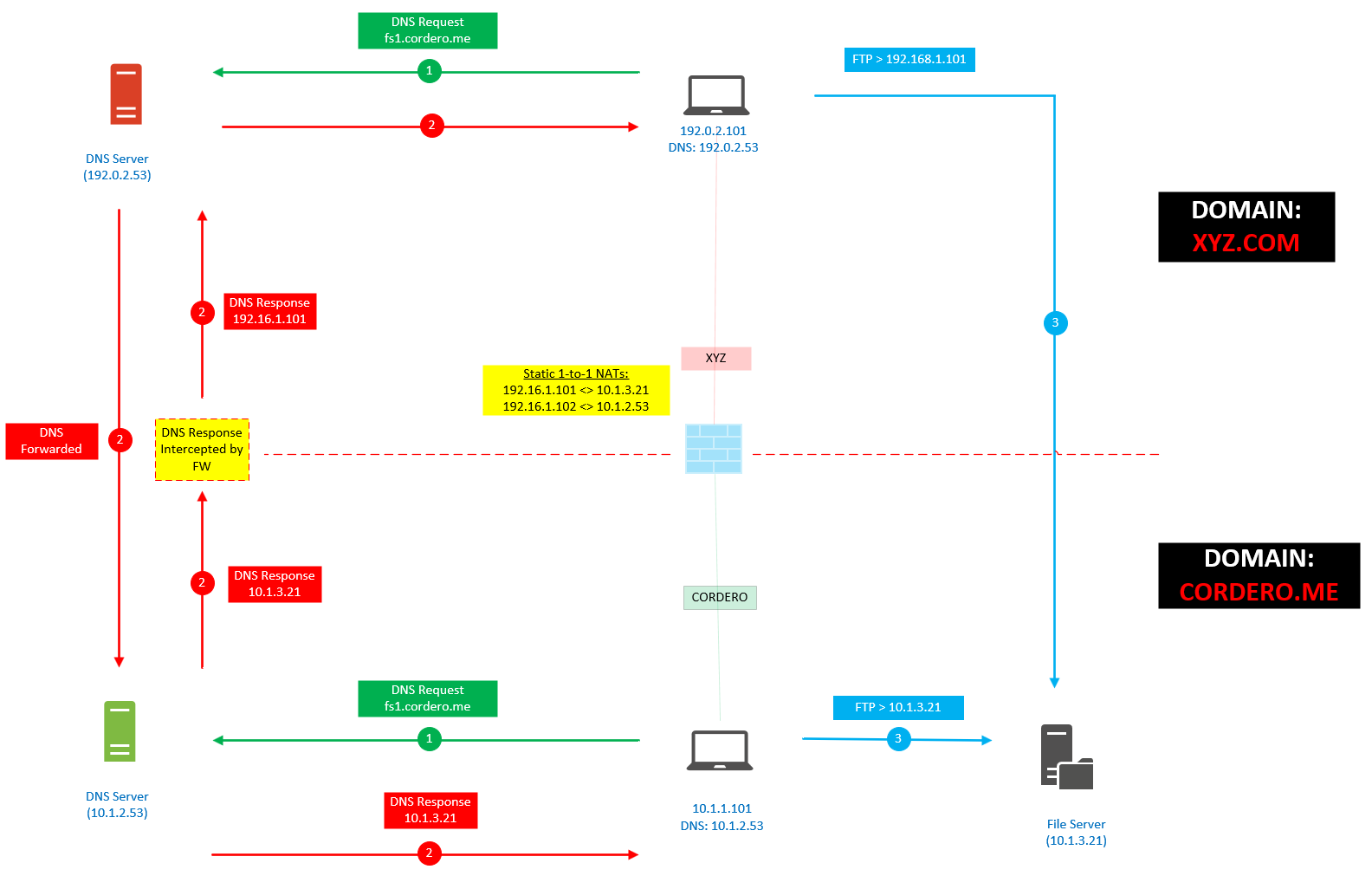
Below I try to demonstrate a way not to create more work and try to utilize an existing Internal DNS server. I suggest testing this in a lab first. Have fun and experiment.