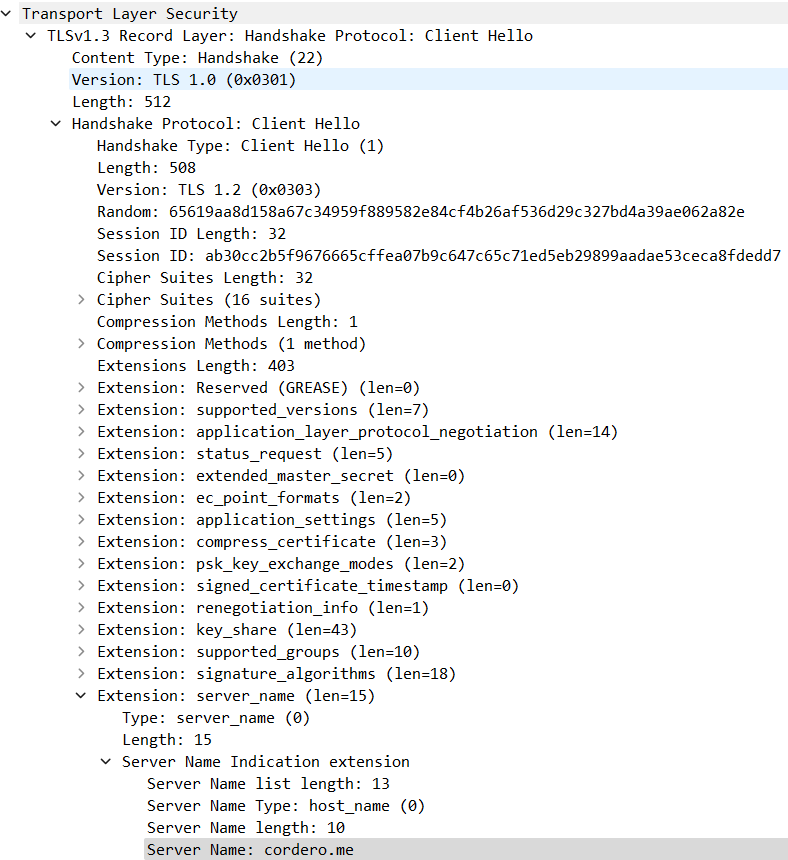
Whenever a Transport Layer Security (TLS) connection begins, the first message sent is the Client Hello. This initial transmission from the Client to the server forms a fundamental part of the TLS protocol (as detailed in RFC5246, 7.4.1.2. Client Hello).
The Client Hello plays a critical role in setting up a TLS session. It establishes parameters such as the TLS version, cipher, resumption, and the requested resource name that the Client can support. This message lays down the ground rules for the forthcoming TLS communication.
Now, how can we peek into the content of these TLS messages? This is where Wireshark, a popular network protocol analyzer, emerges. It offers a powerful TLS packet dissector that deciphers and organizes the data within these encrypted communications.
For instance, when you choose a Client Hello packet from Wireshark’s packet list pane, the tool’s packet dissector takes over. It analyses the Client Hello and presents the significant data in an easily readable format in the packet details pane.
The TLS dissector in Wireshark reveals essential information about TLS communication. The packet details pane shows that the TLS session version is 1.3. Furthermore, by expanding the Server Name Indication (SNI) extension, we can obtain the destination name used within the TLS session.
The SNI, a noteworthy extension within the Client Hello, is a tool the Client uses to inform the server about the specific web identity it is trying to access. This allows the server to pick the correct certificate key pair for the TLS/SSL session and the correct web application. This interaction between the Client and server ensures a smooth and secure TLS/SSL session establishment.
Example
Wireshark Filter:
ip.addr == 74.207.230.63 and tls.handshake
Output:
Transport Layer Security > TLSv1.3 Record Layer: Handshake Protocol: Client Hello > Handshake Protocol: Client Hello > Extension: server_name > Server Name Indication extension