Layer 2 hardening involves implementing various security features and practices to enhance the security and stability of Layer 2 network infrastructure. Let’s explore the commonly used Layer 2 hardening techniques you mentioned:
- RootGuard:
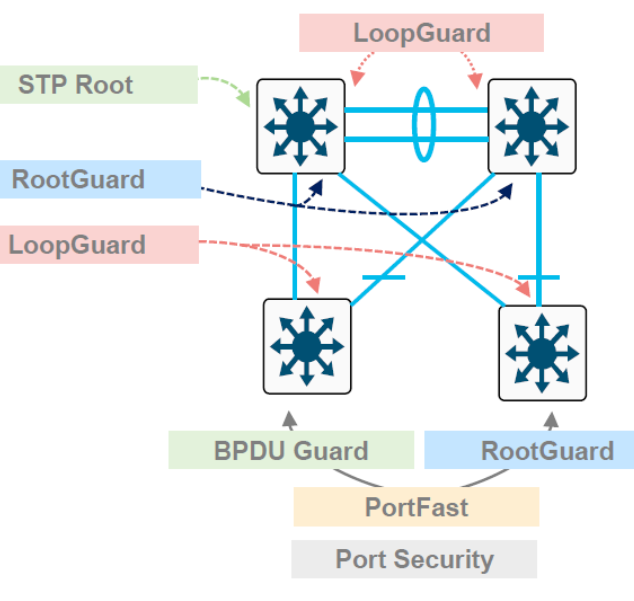
RootGuard is a feature used in spanning tree protocol (STP) environments to protect against unauthorized switches attempting to become the root bridge. RootGuard prevents switches connected to the network from participating in the STP election process as the root bridge, thereby maintaining a secure and predictable network topology.
- LoopGuard:
LoopGuard is a mechanism that helps prevent unidirectional link failures in a spanning tree topology. It detects when BPDUs are not received on designated ports and places them into a loop-inconsistent state, preventing network loops caused by misconfigurations or link failures.
- UplinkFast:
UplinkFast is a Cisco proprietary feature that provides fast convergence in the event of a link failure on an access layer switch. It allows the switch to quickly switch to an alternate designated port, minimizing the downtime for end devices connected to the failed link.
- UDLD (UniDirectional Link Detection):
UDLD is a Cisco proprietary protocol that detects unidirectional links between directly connected devices. It helps identify situations where traffic may flow in one direction but not the other due to a physical connectivity issue or a configuration problem. UDLD allows devices to detect and take corrective actions when unidirectional links are detected, improving the reliability and stability of the network.
- BPDU Guard:
BPDU Guard is a security feature used to protect against accidental or malicious misconfigurations of STP. It shuts down a port if it receives a BPDU, preventing potential STP manipulation or network loops caused by unauthorized switches or misconfigured devices.
- PortFast:
PortFast is a Cisco feature that allows access ports to transition directly from blocking to forwarding state, bypassing the listening and learning phases of the spanning tree. It is used on ports connecting to end-user devices like workstations or printers to expedite connectivity and reduce network convergence time. PortFast should not be enabled on ports connecting to switches or devices that can create loops.
- Port Security:
Port security is a feature that allows you to restrict the number of MAC addresses allowed on an interface. It prevents unauthorized devices from connecting to the network by dynamically learning MAC addresses and associating them with specific switch ports. Exceeding the configured limits on a port can trigger various actions like port shutdown or security violation notifications.
Implementing these Layer 2 hardening techniques helps improve network security, prevent network loops, mitigate misconfigurations, ensure rapid network convergence, and control access to the network. However, it’s important to consider the specific requirements of your network environment and consult the official documentation and configuration guides provided by Cisco or the respective network equipment vendor for detailed instructions and best practices for enabling and configuring these features.