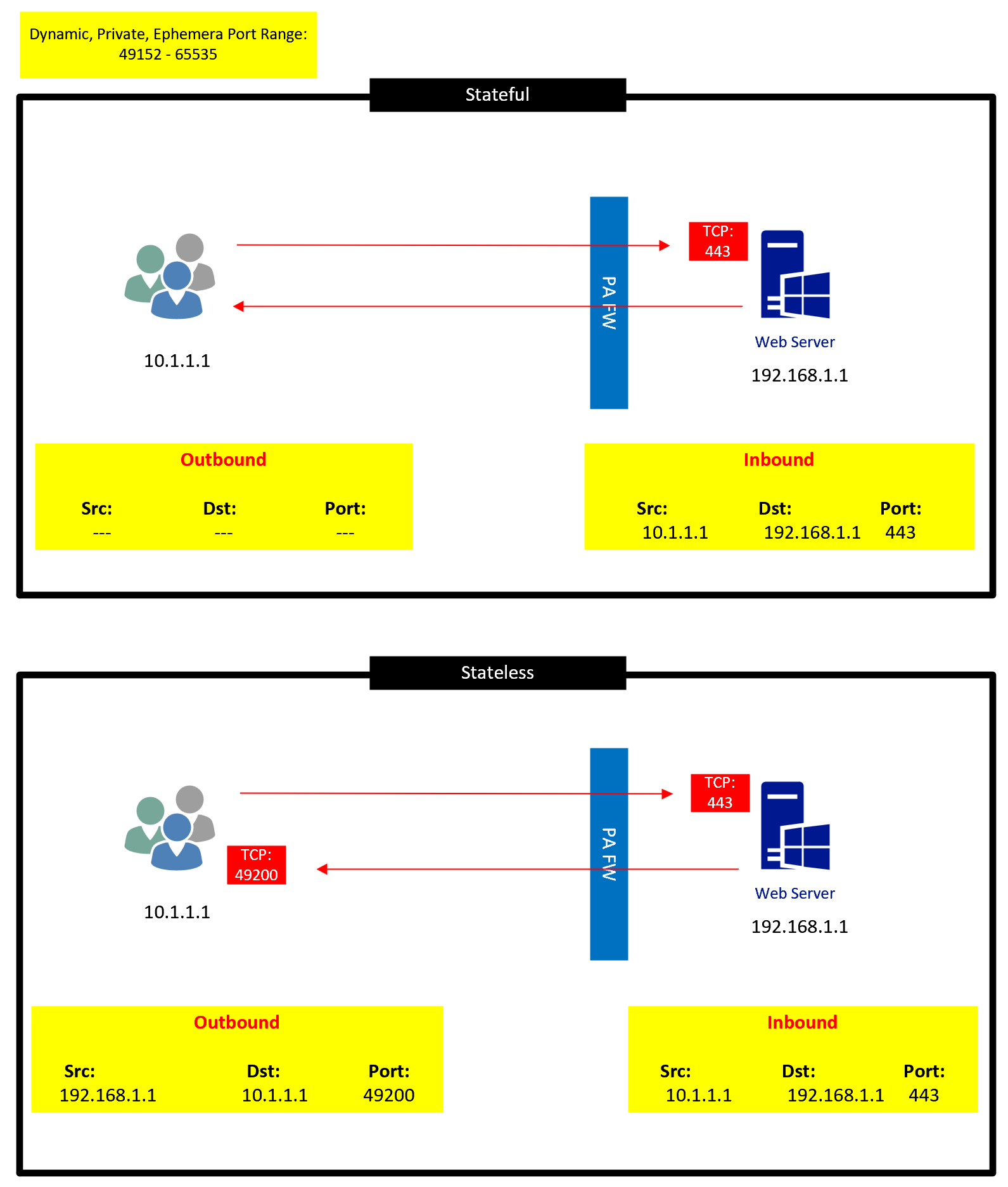
Stateful Firewall
Definition: Stateful firewalls maintain a state table that tracks all active connections and sessions passing through it.
Session Handling:
- Tracks every connection: Remembers details about active connections, such as IP addresses, ports, sequence numbers, and additional protocol-specific parameters.
- Monitors the state of each session: Recognizes the various stages of a connection (e.g., initiation, established, termination).
Decision Making:
- Makes decisions based on the context of the session, as well as static rules.
- Can dynamically allow or deny traffic based on the ongoing state of a connection.
- Checks if the incoming packet is part of an existing connection or is trying to initiate a new one. If it’s part of an established session, it’s typically allowed through. If not, it must pass all the firewall’s rules to be allowed.
Example: Using the same scenario of a user accessing a web server: With a stateful firewall, once the user’s request to the server is allowed and noted in the state table, the returning traffic from the server is automatically recognized as part of the established connection and allowed, even without a specific rule for the return traffic. This makes the process more efficient and reduces the number of rules an administrator must set up.
Stateless Firewall
Definition: Stateless firewalls make decisions based on individual packets in isolation. They do not maintain a state or context about active connections.
Session Handling:
- No memory of past interactions: Each packet is treated as an independent entity without regard to any preceding packets.
- No connection tracking: Does not keep track of active connections or sessions.
Decision Making:
- Based purely on static rules defined by the engineer.
- Uses packet header information like source IP, destination IP, source port, destination port, and protocol type.
Example: Imagine a user trying to access a web server. The outbound request to the server (e.g., HTTPS on port 443) is allowed by a rule on the firewall. However, the returning traffic from the server also needs a specific rule to allow it, even though it’s simply the response to the user’s legitimate request. Without this rule, the response from the server would be dropped, disrupting the user’s access.
Comparison
To sum up, here’s a simple comparison:
- Efficiency:
-
- Stateful: Automatically recognizes and allows return traffic for established sessions, requiring fewer rules.
- Stateless: Requires rules for both outgoing and incoming traffic. Can be less efficient since each packet is treated individually.
- Security:
-
- Stateful: More secure because it can recognize whether an incoming packet is part of an ongoing legitimate session or an unsolicited and potentially malicious request.
- Stateless: Less secure as it lacks the context about ongoing communications. Malicious actors could potentially exploit this by crafting packets that match allowed rules.
- Complexity:
-
- Stateful: Might require more advanced configuration initially, but can reduce administrative overhead in the long run due to its dynamic nature.
- Stateless: Potentially simpler to set up initially, especially in environments with predictable traffic patterns.
In most modern environments, stateful firewalls are preferred due to their enhanced security and ability to reduce the number of necessary rules. However, stateless firewalls or a combination of both might be used in certain situations or specific network segments.