If you’re doing SSL Offloading, you may run across sites that don’t behave well when HTTP/2 Inspection is enabled. You might need to disable HTTP/2 Inspection for those sites. Below is how you do it.
But before you do it, here’s what’s going to happen. ALPN is used to Secure HTTP/2 connections. When you disable it, the firewall downgrades HTTP/2 traffic to HTTP/1.1 or it classifies the traffic as unknown TCP.
The most important thing here is that you only want to do it to specific sites and not do this globally even though I’ll show you how to do this globally. It’s not good for security to turn it off all together. Like I mentioned above, the firewall will classify this traffic as unknown TCP traffic which is not a good thing.
Go to:
Objects > Decryption > Decryption Profile > SSL Decryption > SSL Forward Proxy and then select Strip ALPN.
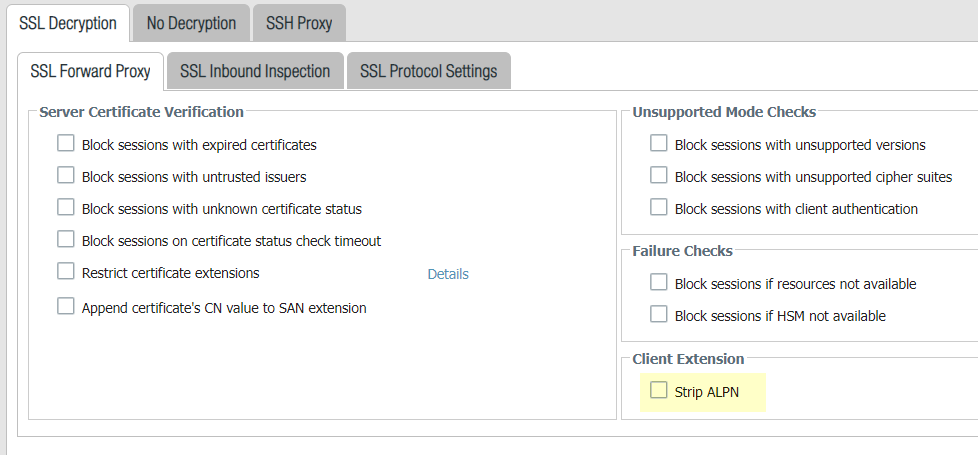
You’ll want to apply this decryption profile to a decryption policy to disable HTTP/2 inspection for traffic that matches that policy.
To disable this globally via CLI:
set deviceconfig setting http2 enable no commit
You can look for HTTP/2 traffic in your logs:
Monitor > Logs and check the HTTP/2 Connection field