There might be times where you need to import an Intermediate CA because the FW is restricting access to a site when SSL-Decryption is enabled. The Palo Alto firewall does not trust the Intermediate CA. So you are adding the Intermediate Cert to the Palo manually and trusting it as a CA. I’m not a big fan of this process because I don’t want to start getting into certificate management which is already a nightmare if you don’t have a proper team handling them. If a site is not configured correctly, contact that site to fix it. I know this doesn’t always work, but they should know about it. I would instead add these to the SSL-Decrypt Exclude list and check on the site to see if they make the fix. If not, keep it excluded from SSL Decryption. Best practices always mention using the exclude list, and I’ve never seen where they tell you to go out and export/import certs. I’m not saying you shouldn’t do it because not all environments are the same, but I’d stick with the exclusion list. Chances are this is a client you work with and there’s already a specific rule locked down for this access which is being logged.
#HOW TO GET THE INTERMEDIATE CERT
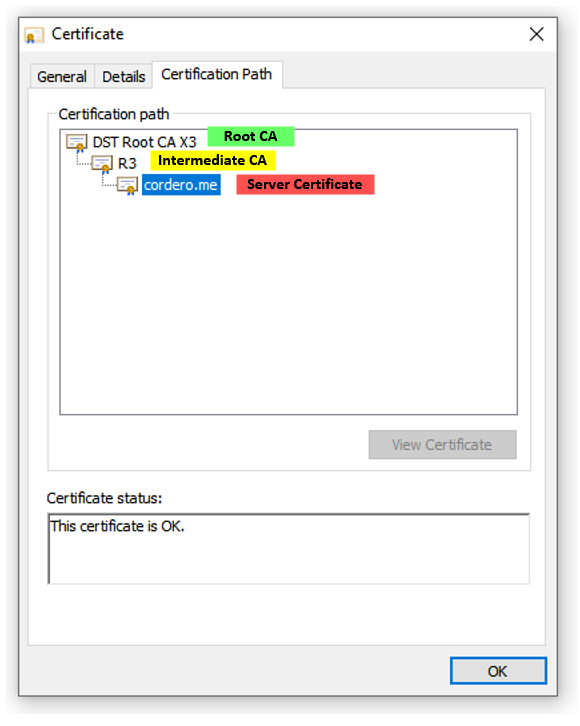
1. Go to the site, right click the lock next to the domain name and select “Certificate”
2. Click on the “Certificate Path” tab.
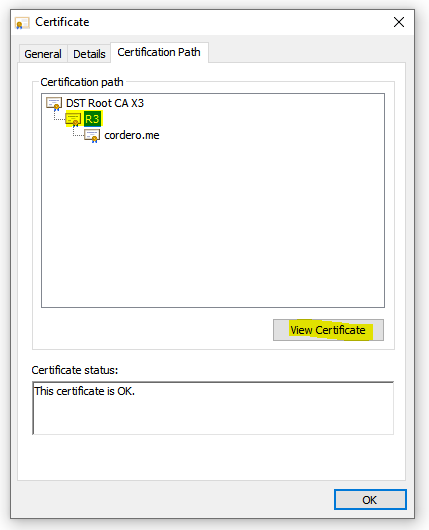
3. Look for the Intermediate CA and click on it
4. Now click on “View Certificate”
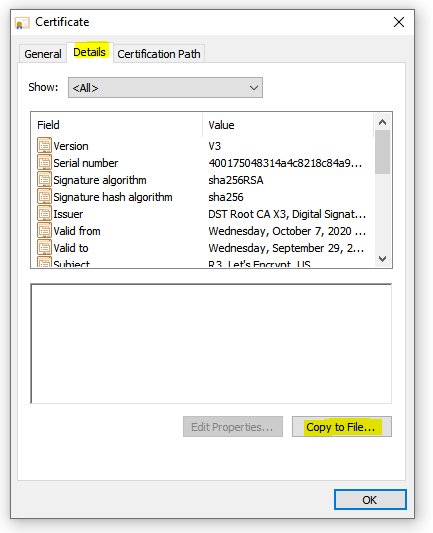
5. Go to the “Details” tag and clock on “Copy to File…”
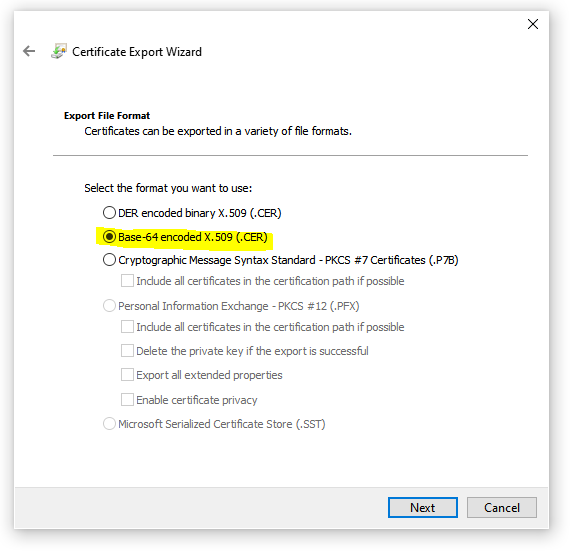
6. On the next screen click on “Next”
7. Now select the format you want to export to which should be “Base-64 encoded X.509 (.CER)“.
8. Follow the rest of the export process to save the cert.
#HOW TO IMPORT THAT INTERMEDIATE CERT INTO THE PALO ALTO
1. Login to the firewall through the WebGUI
2. Go to Device > Certificates > Import > Import “Intermediate Cert” “R3”
3. Click on the certificate and check “Trusted Root CA“.