SAML (Security Assertion Markup Language) is an XML-based open standard used for exchanging authentication and authorization data between parties, primarily in web-based single sign-on (SSO) scenarios. SAML enables the secure sharing of user identity and access information across different domains or organizations.
Here are the key aspects, benefits, and best practices of implementing SAML:
How SAML Works:
SAML involves three main entities: the identity provider (IdP), the service provider (SP), and the user. The IdP is responsible for authenticating the user and generating a security assertion, while the SP consumes the security assertion to grant access to resources. The user initiates the authentication process by accessing a protected resource on the SP, which redirects the user to the IdP for authentication. Upon successful authentication, the IdP generates a SAML response containing assertions about the user, which is sent back to the SP. The SP validates the response and grants access to the requested resource.
Benefits of SAML:
- Single Sign-On (SSO): SAML enables users to access multiple applications or services with a single set of credentials, improving usability and user experience.
- Security and Trust: SAML uses digital signatures and encryption to ensure the integrity and confidentiality of data exchanged between the IdP and SP, enhancing security and preventing tampering or eavesdropping.
- Federation and Collaboration: SAML facilitates secure identity federation across different organizations or domains, enabling seamless access to shared resources.
- Centralized Access Control: With SAML, access policies and user attributes can be managed centrally at the IdP, allowing consistent and granular control over user access across multiple applications.
- Compliance and Auditing: SAML supports the tracking and auditing of user access, helping organizations meet regulatory and compliance requirements.
Best Practices for Implementing SAML:
- Understand Requirements: Identify the specific use cases, integration requirements, and desired level of security and control before implementing SAML.
- Choose a Reliable Identity Provider: Select a well-established and trusted identity provider that aligns with your organization’s security requirements and offers comprehensive SAML support.
- Secure SAML Communications: Implement secure protocols like HTTPS for SAML communication to protect data in transit and prevent man-in-the-middle attacks.
- Properly Configure Identity Provider and Service Provider: Ensure accurate configuration of both the IdP and SP, including certificates, entity IDs, endpoints, and attribute mappings.
- Regularly Update and Patch Software: Keep the IdP and SP software up to date with the latest security patches and fixes to address vulnerabilities.
- Test and Monitor: Thoroughly test the SAML integration and regularly monitor its performance and security. Conduct periodic security assessments and penetration testing.
- Educate Users: Provide clear instructions and educate users on how to access SAML-enabled services and handle any potential authentication challenges.
By following these best practices, organizations can implement SAML effectively, enhance security, streamline user access, and simplify identity management across various applications and services.
Example:
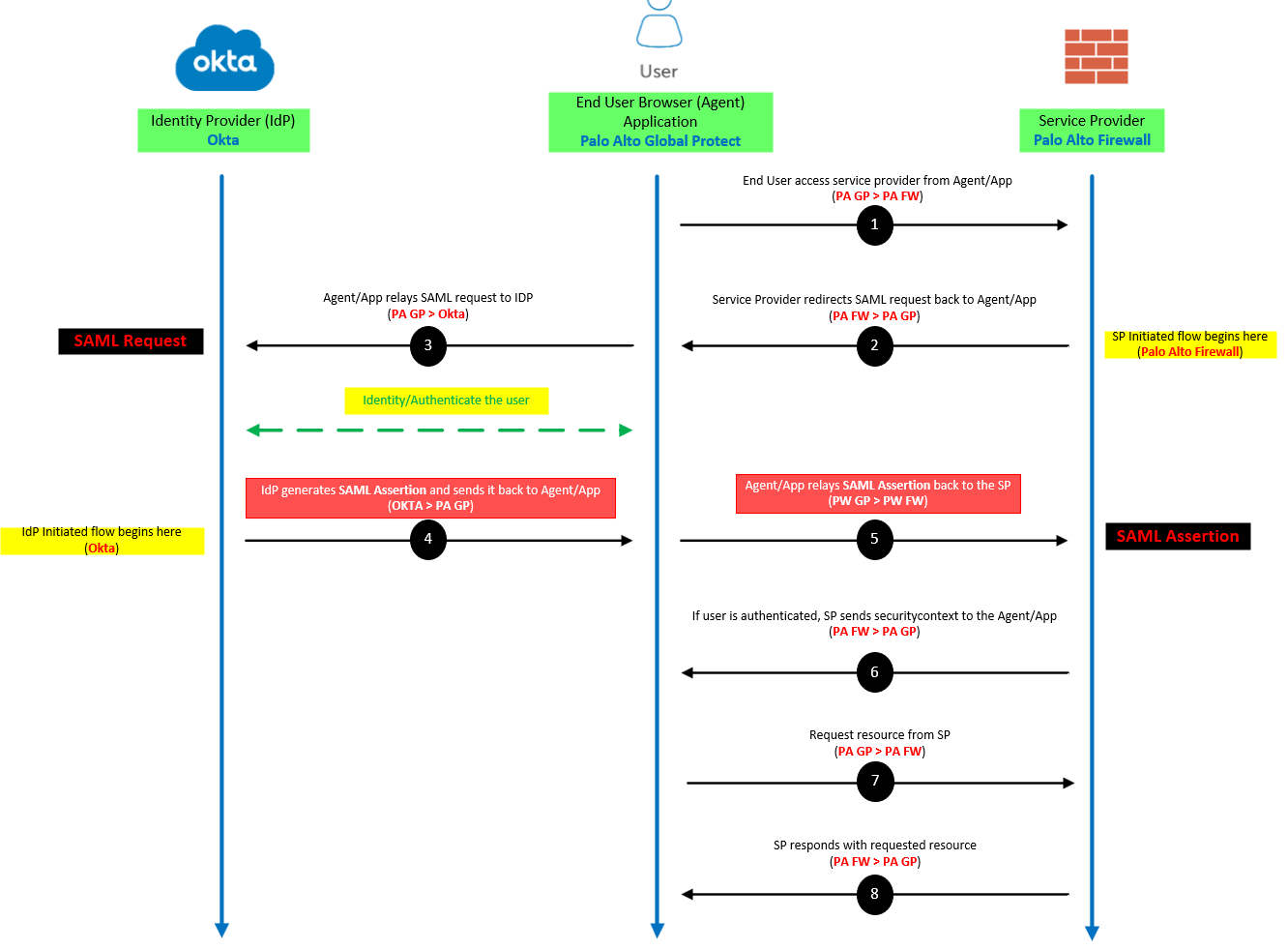
SAML is everywhere nowadays, which means it’s used a lot for many scenarios and applications. My example is with Palo Alto Global protect, but there’s not much difference when using it for something like Office365 web apps.
Service Provider (SP) – Palo Alto Networks Firewall
Identity Provider (IdP) – Okta
Application – GlobalProtect VPN App
- A Service Provider (SP) is the entity providing the service, typically in the form of an application.
- An Identity Provider (IdP) is the entity providing the identities, including the ability to authenticate a user. The Identity Provider typically also contains the user profile: additional information about the user such as first name, last name, job code, phone number, address, and so on. Depending on the application, some service providers may require a very simple profile (username, email), while others may require a richer set of user data (job code, department, address, location, manager, and so on).
- A SAML Request, also known as an authentication request, is generated by the Service Provider to “request” an authentication.
- A SAML Response is generated by the Identity Provider. It contains the actual assertion of the authenticated user. In addition, a SAML Response may contain additional information, such as user profile information and group/role information, depending on what the Service Provider can support.
- A Service Provider Initiated (SP-initiated) sign-in describes the SAML sign-in flow when initiated by the Service Provider. This is typically triggered when the end user tries to access a resource or sign in directly on the Service Provider side, such as when the browser tries to access a protected resource on the Service Provider side.
- An Identity Provider Initiated (IdP-initiated) sign-in describes the SAML sign-in flow initiated by the Identity Provider. Instead of the SAML flow being triggered by a redirection from the Service Provider, in this flow the Identity Provider initiates a SAML Response that is redirected to the Service Provider to assert the user’s identity.
SAML ASSERTIONS
SAML assertions are the messages exchanged between an identity provider (IdP) and service provider (SP) that confidentially identify who a user is, what pertinent information exists, and what they’re authorized or entitled to access.
Sources:
https://developer.okta.com/docs/concepts/saml/#planning-for-saml
https://saml-doc.okta.com/SAML_Docs/How-to-Configure-SAML-2.0-for-Palo-Alto-Networks-GlobalProtect.html