HOW CERTIFICATE CHAINS WORK
Certificate chains, also known as a chain of trust, work on the concept of Public Key Infrastructure (PKI). This system utilizes digital certificates to authenticate and verify the identity of individuals, servers, or devices over the internet.
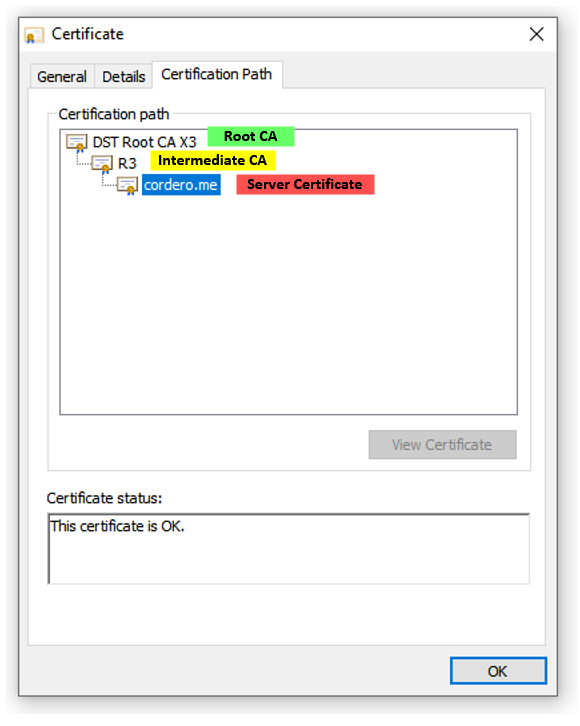
A certificate chain consists of several certificates linked together, starting with the end-user’s certificate (also known as the subscriber or server certificate), followed by one or more intermediate certificates, and ending with a root certificate.
Here’s how it works:
- The root certificate belongs to a trusted Certificate Authority (CA). It is self-signed, which means that the entity that it represents is also the entity that has verified and signed it. This root certificate is stored in web browsers and operating systems.
- Intermediate certificates act as a bridge between the root and the end-user certificates. These certificates are issued by the root CA or by another intermediate CA that is trusted by the root CA.
- The end-user certificate is the one installed on your server. It is issued by one of the intermediate CAs.
During the SSL/TLS handshake, the server presents the client with this chain of certificates. The client verifies each certificate in the chain against its issuer, all the way up to the trusted root certificate. If this verification is successful, the client can trust the server’s identity and establish a secure connection.
COMMON ISSUES
Common issues with certificate chains include:
- Incomplete or Incorrect Certificate Chains: Sometimes, the server might not send all of the necessary intermediate certificates, or the order of the certificates in the chain could be incorrect. Both cases can lead to chain validation failures.
- Expired Certificates: Certificates are valid only for a certain period. If a certificate in the chain (root, intermediate, or end-user) expires, the chain will break, and the SSL/TLS handshake will fail.
- Revoked Certificates: If any certificate in the chain is revoked by the issuing CA, the entire chain becomes invalid.
- Untrusted Root Certificates: If the root certificate is not trusted by the client (not included in the client’s root store), the certificate chain will not be trusted.
RECOMMENDATIONS
To mitigate these issues, consider the following recommendations:
- Proper Certificate Installation: Ensure that all necessary certificates, including intermediate certificates, are correctly installed on the server and presented in the correct order.
- Regularly Update and Check Certificate Validity: Regularly check the validity of your certificates and renew them before they expire. Many systems provide alerts when certificates are nearing their expiry dates.
- Monitor for Certificate Revocation: Keep an eye on the Certificate Revocation List (CRL) or use the Online Certificate Status Protocol (OCSP) to check if a certificate has been revoked.
- Use Trusted Certificate Authorities: Always use certificates issued by a trusted CA. The root certificate of this CA should be present in the trust store of the client’s browser or operating system.
- Automate Certificate Management: Consider using automated certificate management solutions, which can automate the tasks of issuing, renewing, and revoking certificates.
- 6. Regularly Update Your Systems: Keep your systems updated so they recognize the latest trusted root certificates.
Remember, a well-managed certificate chain is a critical part of maintaining secure connections and ensuring the integrity and trustworthiness of your website or service.
EXAMPLE
When you connect to a secure website (HTTPS), here’s a step-by-step process of how certificate chains work:
- Certificate Presentation: The server, in this case cordero.me, presents your browser with its SSL/TLS certificate, which includes the server’s public key. This certificate is digitally signed by a trusted Certificate Authority (CA). It also may present intermediate certificates linking its own certificate to a higher-level authority.
- Certificate Validation: Your browser starts validating the server’s SSL/TLS certificate. It begins by validating the digital signature on the server’s certificate using the public key of the CA that issued it. If the server provided intermediate certificates, this process will be repeated up the chain. Each intermediate certificate is validated using the public key of the CA that issued it.
- Root Certificate Trust: The validation process continues until your browser reaches a certificate that’s already stored in its trusted store, usually a root certificate. Browsers and operating systems come pre-installed with a set of trusted root certificates, so the browser can verify this root certificate without needing further validation.
- Certificate Chain Verification: If each certificate in the chain is successfully validated, the browser trusts the server’s SSL/TLS certificate. This is because there’s a chain of trust extending from the server’s certificate to a trusted root certificate.
- Secure Connection Establishment: Now that the server’s identity has been verified, your browser uses the server’s public key to set up a secure connection.
If the server’s certificate can’t be validated (for instance, if a CA in the chain isn’t recognized, or if a certificate has expired), the browser will warn the user that the connection isn’t secure. The user can then decide whether to proceed or not.
Please note, you can often view the certificate chain of a website in your browser by clicking on the padlock icon in the URL bar and looking for a section related to certificates. The details may vary based on the browser you are using.