DNS name servers are usually split into two categories:
a. Authoritative name servers
b. Non-authoritative name servers or Recursive name servers
Authoritative
This server holds the records for a domain. It controls which records are being used. This is where you go to add new A/CNAME/MX records within a portal. You are in control of the records.
Non-authoritative/Recursive
This server does NOT hold any record for a domain but instead has a cache file that was built with all the DNS lookups it has performed in the past which received an authoritative response. If there’s not record in it’s cache, it will look for the Authoritative.
Below are some examples of what a NSLOOKUP looks like with both an Authoritative and Non-Authoritative/Recursive lookup.
NON-AUTHORITATIVE/RECURSIVE:
Server: b.resolvers.Level3.net
Address: 4.2.2.2
Non-authoritative answer:
Name: www.xyzsite.com
Address: {Public IP}
So above the Level3 External DNS server had the request cached. The request didn’t have to go to the Authoritative DNS server.
AUTHORITATIVE:
Server: {Local Internal DNS Server FQDN}
Address: {Private Local DNS Server IP}
Name: www.xyzsite.com
Address: {Private IP}
Now that we are using the internal DNS and it had the record.
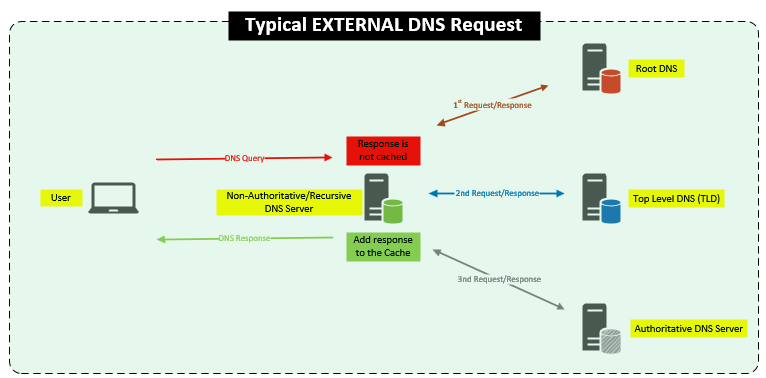
Below are some examples for the flow of DNS queries. This is something to keep in mind when it comes to troubleshooting DNS or just designing your DNS.
The first one is an example of a typical External DNS lookup. This means you don’t have a local DNS on site. This what everyone who uses the internet experiences when they are at home or on their phones. The Non-Auth/Recursive server is given out to you by the ISP. But some people manually config them because some are quicker than others on lookups.
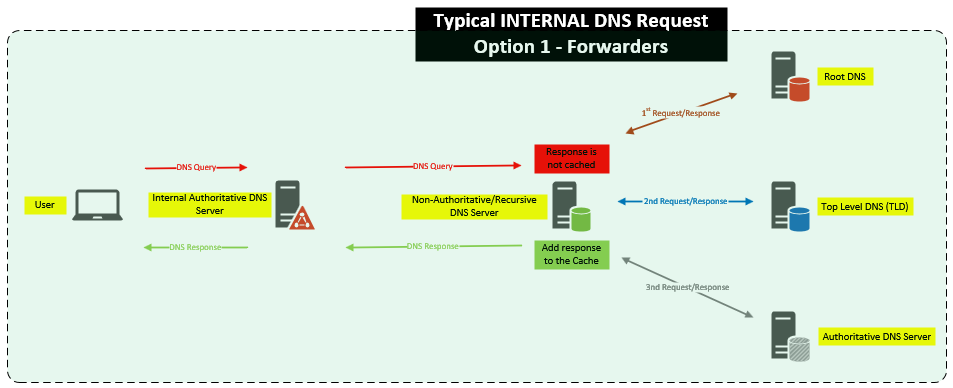
Now we move internal. This is different because you now have a local DNS server setup with Zones. The Zone is your companies “bought” DNS domain name. In my example above, my made up company XYZSite LLC bought XYZSite.com. You don’t need to Split DNS where you have the same domain EXTERNAL and INTERNAL but for our example we are since a lot of companies do this. You could always use XYZSite.local or something like that but that’s not what I’m focusing on. If a Zone is configured on that DNS server, then that server is the Authoritative for that Zone. Any DNS request that comes in for that Zone, that DNS server will handle the lookups.
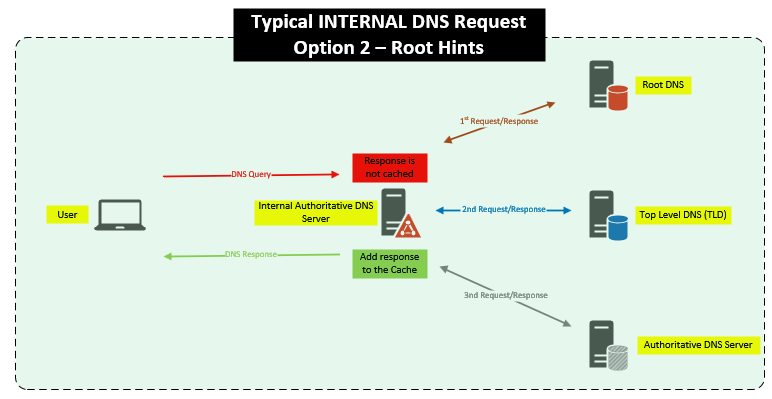
If your internal DNS server does not have a Zone for a DNS request, for example we have a user trying to go to “cisco.com“, we obviously don’t own “cisco.com” and we shouldn’t have a Zone for it, this will leave the internal DNS server with two options:
a. Forwarders – You can choose which Non-Auth/Recursive servers to use. If you don’t set this, it will use Root Hints. If the Forwarders go down for any reason, it will use Root Hints.
b. Root Hints – These are already setup but the Forwarders take priority over these if you set the Forwarders.
NOTE:
You have another option called “Conditional Forwarders“. I blogged about these already but they basically help resolve domain names/Zones that you don’t have Authoritative control over. Going back to my example above, a user now does a DNS request for “abcsite.us“. We “trust” “abcsite.us” because we bought them out and they are part of the same company. They are family. Or you just have a second domain internally to keep it simple. The local DNS server will see it has a “Conditional Forwarder” for the domain “abcsite.us” and it will forward that request to the DNS server that handles that domains Zone (Authoritative server for that domain) to resolve it.