SSL Offloading (or SSL Termination)
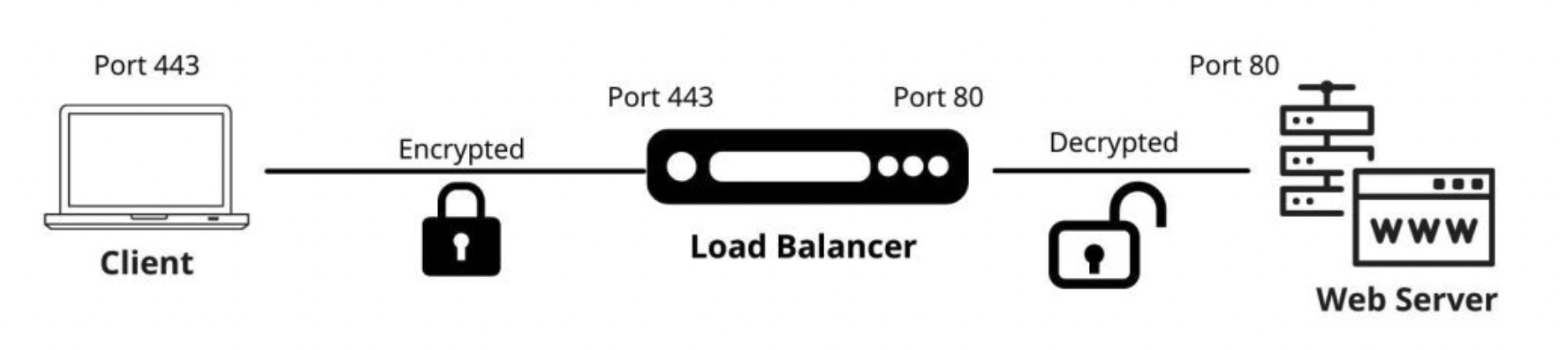
In this method, SSL traffic is terminated at the F5 BIG-IP system, decrypted and inspected, but is not re-encrypted before being forwarded to the server. The BIG-IP system maintains the SSL session with the client, and the server session is over plain HTTP.
Pros:
- Offloads the CPU-intensive task of encryption/decryption from the server, potentially improving server performance.
- Provides the ability to inspect, manipulate, and manage the SSL traffic since it’s decrypted at the load balancer.
- Enables use of security features like F5’s ASM or WAF because the traffic can be inspected.
Cons:
- Traffic between the load balancer and servers is not encrypted, which could pose a security risk if the internal network is not secure.
- Not suitable for applications or environments where end-to-end encryption is a requirement.
SSL Bridging (or SSL Forward Proxy)
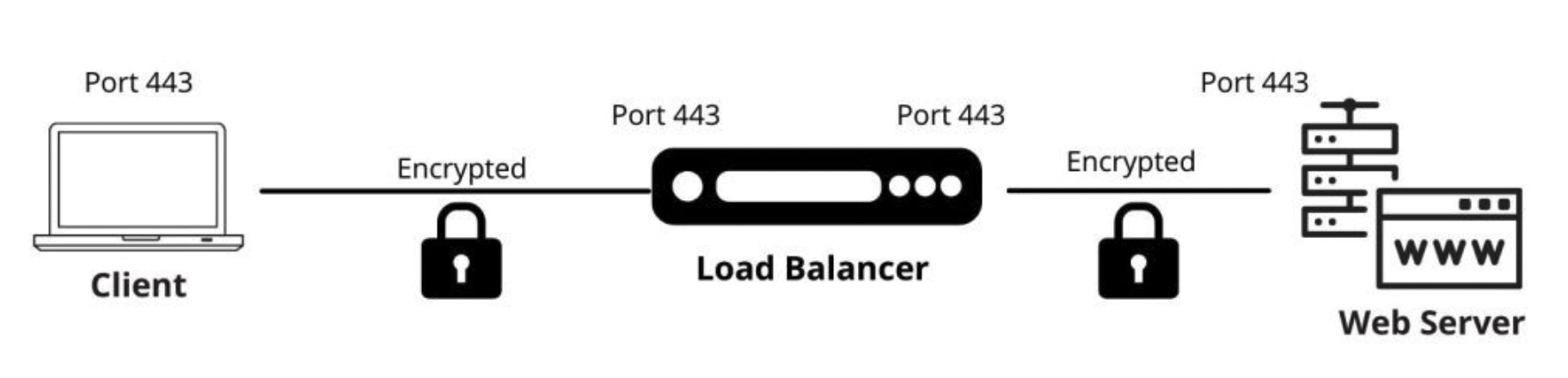
In this method, SSL traffic is terminated at the F5 BIG-IP system, decrypted and inspected, then re-encrypted and forwarded to the server. The BIG-IP system maintains two separate SSL sessions, one with the client and one with the server.
Pros:
- Offers the highest level of security as traffic is encrypted throughout its journey, except while being inspected at the load balancer.
- Provides the ability to inspect, manipulate, and manage the SSL traffic since it’s decrypted at the load balancer.
- Enables use of security features like F5’s ASM or WAF because the traffic can be inspected.
Cons:
- Performance overhead is higher as there are two separate SSL sessions to manage (client-side and server-side).
- More complex to manage, as SSL certificates must be maintained on both the BIG-IP system and the servers.
SSL Passthrough
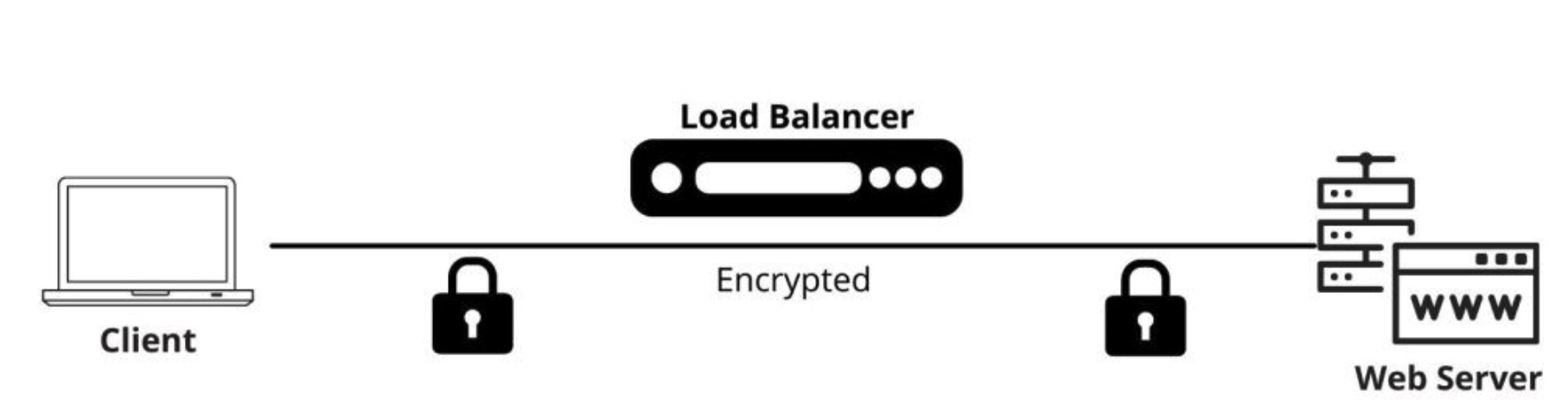
In this method, SSL traffic is not decrypted at the F5 BIG-IP system at all. It is simply forwarded directly to the servers, which handle the encryption/decryption. The SSL session is maintained between the client and server, with the BIG-IP system simply passing the traffic along.
Pros:
- SSL traffic is encrypted end-to-end, from the client to the server, offering a high level of security.
- No need to manage SSL certificates on the BIG-IP system, simplifying certificate management.
Cons:
- The BIG-IP system cannot inspect or manipulate the SSL traffic because it’s always encrypted.
- Security features that require traffic inspection, like F5’s ASM or WAF, cannot be used with SSL passthrough.
- Places the CPU-intensive task of encryption/decryption on the server, which could impact server performance.
Each method has its own use cases, and the choice between them depends on your specific needs in terms of performance, security, manageability, and compliance with any relevant regulations or policies.