UPDATE:
In Panorama PAN-OS 10.X: You cannot use the ‘equal-to‘ operator for custom signatures in this use case. The ‘negate‘ checkbox option was added to the ‘equal-to‘ operator starting in PAN-OS 10.X.
This means you have now have to use “less-than” and “greater-than” instead of “equal-to“.
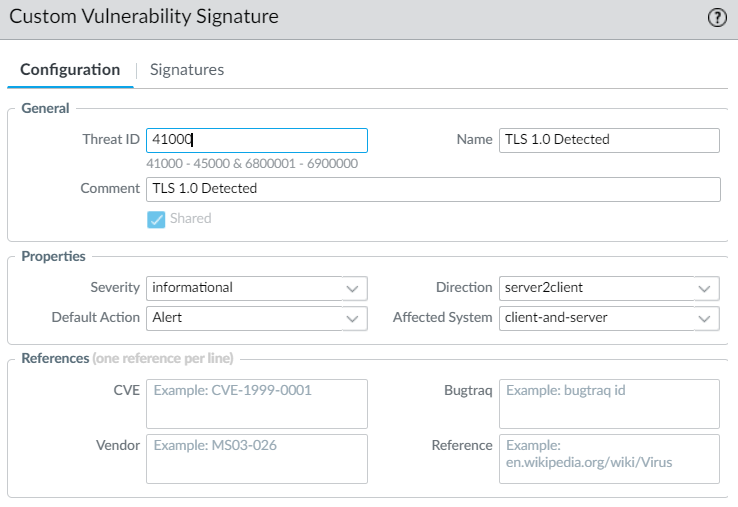
CUSTOM VULNERABILITY SIGNATURE
OBJECTS > Custom Objects > Vulnerability
Build out your “Custom Vulnerability Signature”:
NOTE:
The threat ID’s from 41000 to 45000 are reserved for Custom Vulnerability signatures.
Please Note:
Severity: informational (You have change this)
Default Action: Alert
Direction: server2client
Affected System: client-and-server
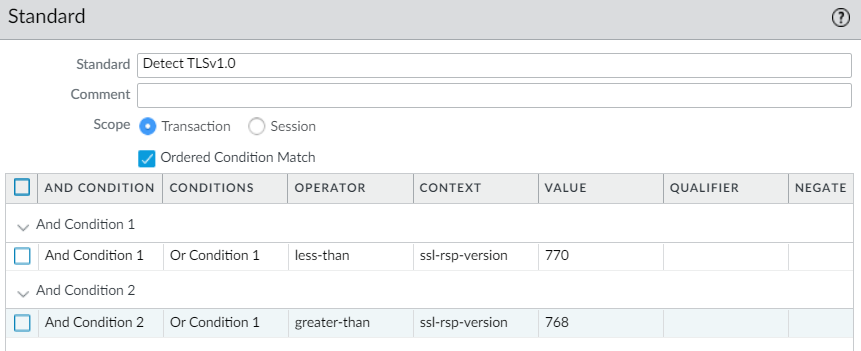
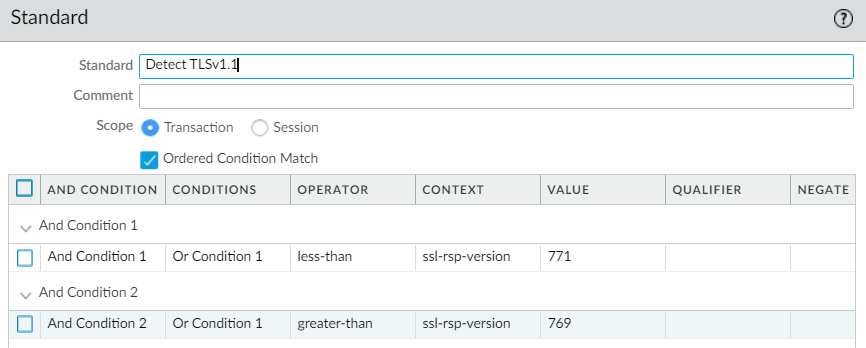
Signature Tab Configurations:
TLS 1.0:
Less Than: 770 (TLS 1.1)
Great Than: 768 (SSL 3.0)
TLS 1.1:
Less Than: 771 (TLS 1.2)
Great Than: 769 (TLS 1.0)
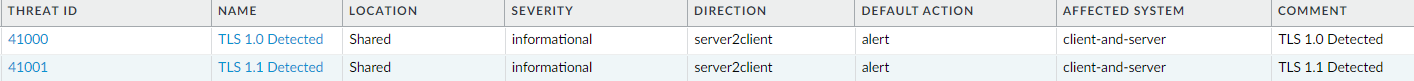
Below is what they will look like when completed:
VULNERABILITY PROTECTION PROFILE
OBJECTS > Security Profiles > Vulnerability Protection
You will now have to “ENABLE” that two new Custom Vulnerability Signatures in your “Vulnerability Protection Profile“:
TLS DECIMAL TABLE
| TLS 1.2 | 0x0303 | 771 decimal |
| TLS 1.1 | 0x0302 | 770 decimal |
| TLS 1.0 | 0x0301 | 769 decimal |
| TLS 1.3 | 0x0304 | 772 decimal |
| SSL 3.0 | 0x0300 | 768 decimal |
| SSL 2.0 | 0x0002 | 2 decimal |