Understanding the behavior of TCP retransmissions in packet capture, particularly in the context of companies that whitelist IP addresses, is crucial for network troubleshooting and security. This behavior, which is expected and a result of how TCP operates with strict whitelisting policies, can significantly impact network performance and security.
When a client initiates a TCP connection with a server that has whitelisted IP addresses, the server’s firewall plays a critical role. If the client’s IP address is not on the whitelist, the firewall, which is configured to block all traffic from non-whitelisted IP addresses, will drop the client’s initial SYN packet. This action sets in motion the sequence of TCP retransmissions.
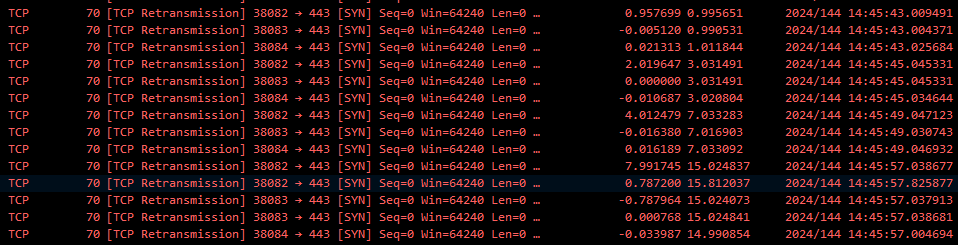
Undeterred by the lack of response, the client, unaware of its SYN packet being dropped, persists in retransmitting it after a certain timeout period (typically a few seconds). This tenacious process continues, with the client steadfastly retransmitting the SYN packet until it either receives a response from the server or exhausts the maximum number of retransmission attempts.
In a packet capture (see below), you will see these retransmitted SYN packets from the client as TCP retransmissions. The number of retransmissions you see will depend on the client’s TCP retransmission timeout settings and the maximum number of retransmission attempts allowed.
Once the client’s IP address is whitelisted on the server’s firewall, the server will respond to the client’s SYN packet, and the TCP connection can be established generally without further retransmissions.
As more and more companies adopt IP whitelisting, the use of packet capture becomes increasingly valuable. This tool can effectively indicate whether the client or vendor is whitelisting IPs, empowering you with crucial information.